The most effective way to protect domains is to add an extra level of security, known by the acronym DNSSEC – Domain Name System Security Extensions. Adding it to a domain is easy, just ask your Authorised Registrar (more information below).
What is it?
How does it work?
In that short time, while the DNS is „translating“ the domain into an IP address, sensitive data may be redirected, stolen or misused. So you may appear on a seemingly identical page, but in reality it is not so. Even the address bar in the browser looks the same like you entered it there.
Thus, the average user does not have a chance to recognize that his device is under attack.
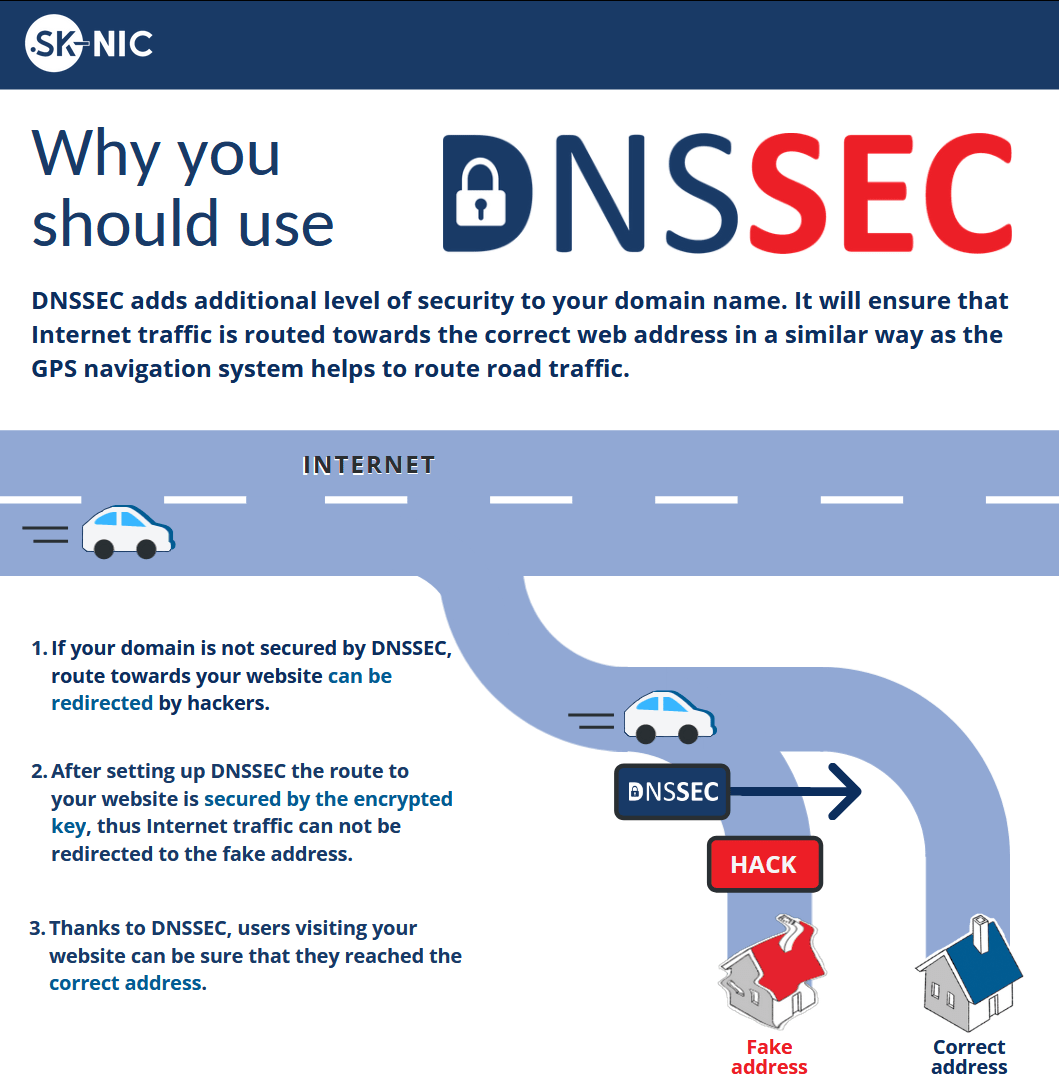
Why DNSSEC?
After all you don’t want the users of your website to end up in the hands of scammers!
Video
How do I know if a domain has DNSSEC?
After loading this website simply write the domain to the search box, including the .sk extension, and the system will provide all available data to you. Red color and also an alert icon will alarm you that the domain is not secured by the DNSSEC service.
In some web browsers, there may also be available an extension that allows you to view similar information directly through the browser.
Where can I get it for my domain?
DNSSEC Statistics for .sk
What is the technology behind DNSSEC?
DNSSEC is using asymmetric encryption – one key for encryption and another one for decryption. Similar principle is being used for encryption and electronic signing of emails (OpenPGP, S/MIME). Holder of the domain that uses DNSSEC generates pair of keys – one private key and one public key (or its registrar provides these keys). Technical details of the domain are subsequently electronically signed by the private key. Public key, stored with the superior authority of the domain, is then used for verification of the authenticity of the technical data through verification of the validity of this signature via the entire hierarchy of the superior signatures all the way to the root one.
After launch of DNSSEC, the technical data of the top level domain .sk will be signed and registry manager SK-NIC, a.s. will hand over the public key to this signature to its own superior authority – to the worldwide manager of the root servers of DNS. This will create hierarchy which will ensure credibility of the data as long as it is not breached at any point, i.e. unless there are errors or misconfigurations, and thus providing that all electronic signatures are all right.
Security Bottlenecks of DNS
In time of creation of the DNS system at the beginning of 80-ties, there was no special attention paid to the security mechanisms of this protocol. Computers of that time were significantly less powerful, asymmetric cryptography (using pair of public and private keys) was still just a new concept and global computer network was significantly smaller with relatively lower number of interconnected people and institutions who mutually knew each other. Over the past 30 years, the use of internet increased dramatically and the DNS protocol became vulnerable, which required creation and use of additional security mechanisms.
There are several major security risks of the DNS system:
- DNS hijacking: Computer is opening the website using the IP address provided upon the query to the DNS server. In the case of DNS hijacking, the attacker changes the DNS settings of the computer in such a way, that whenever the computer sends DNS query for IP address translation, instead of the authentic DNS of the internet provider the computer is connected to the false DNS server controlled by the attacker. Such an attack usually occurs if there is a malicious code infection within the computer, e.g. DNS altering trojan. The malicious code changes the DNS settings and replaces address of the authentic DNS server by the address of the malicious server after it infects the computer. As a result, the affected computer would not receive the correct IP address of the requested webpage, but the malicious IP address which is directing the user’s traffic to the website of the attacker and the web browser thus displays a malicious website.
- DNS Cache Poisoning: By DNS cache poisoning we call a situation when instead of the authentic record, malicious data are stored in the cache memory of a computer. For example, if we enter website “sk-nic.sk” for the first time, our computer will send the DNS query to the corresponding DNS server and its answer is stored in DNS cache memory together with the time stamp specifying how long this record is valid. If during this time period we again enter “sk-nic.sk”, our computer will not be asking the DNS server, but will retrieve IP address from the DNS cache memory. In the case of cache poisoning, DNS attackers are using malicious tricks in order to force the computer to save false DNS records containing IP addresses of malicious websites controlled by the attackers. It’s obvious what can happen once these are used.
- Electronic mail: When email messages are being sent from one server to another, the email servers are sending DNS query along in order to receive IP addresses of the email servers corresponding to the email addresses of the recipients. In this case, the attackers can utilize their malicious methods to force email servers to redirect all or selected electronic mail to the servers of the attacker, whereas attackers can subsequently obviously read all the (sensitive) data contained in the email.
However, this list of security risks is not exhausting, there exists other threats as well.
DNSSEC helps to secure against these as well as other forms of attack.