Najúčinnejším spôsobom ochrany domény je pridať k nej doplnkovú úroveň zabezpečenia, známu pod skratkou DNSSEC – Domain Name System Security Extensions. Pridanie k doméne je ľahké, stačí požiadať svojho autorizovaného registrátora (viac informácií nižšie).
Čo je to?
Ako to funguje?
Za ten krátky čas, kým si DNS „preloží“ doménu do IP adresy, môže dôjsť k presmerovaniu, krádeži alebo zneužitiu citlivých údajov. Môžete sa tak ocitnúť na zdanlivo identickej webovej stránke, no v skutočnosti to tak nie je. Dokonca aj adresný riadok v prehliadači vyzerá rovnako, ako ste ho tam pôvodne zadali.
Bežný užívateľ teda nemá šancu rozoznať, že práve prebieha útok na jeho zariadenie.
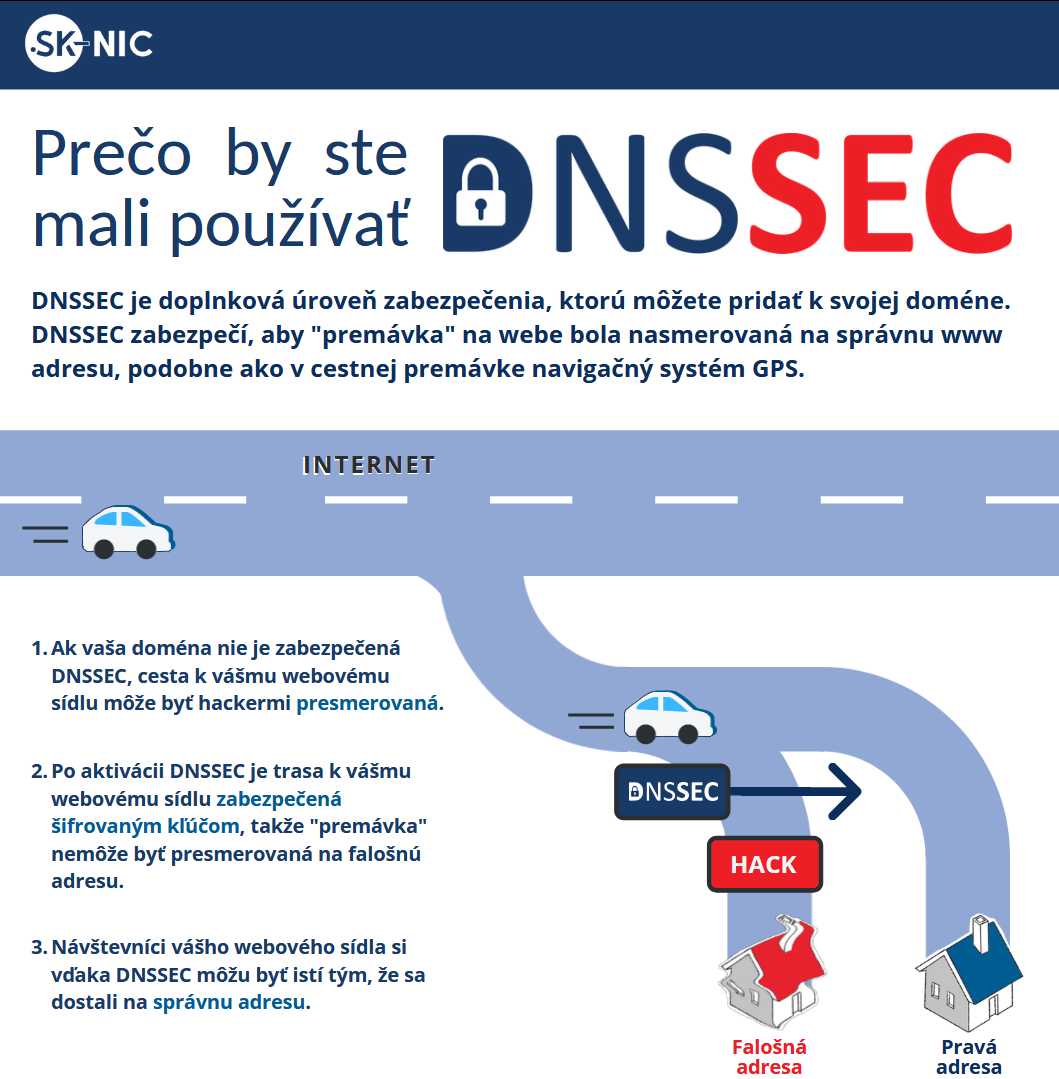
Prečo DNSSEC?
Nechcete predsa, aby používatelia vašej webstránky skončili v rukách podvodníkov!
Video
Ako zistím, či má doména DNSSEC?
Po načítaní tejto webstránky do hľadáčika jednoducho napíšete celé znenie domény, vrátane koncovky .sk, a systém vám poskytne všetky dostupné údaje. Červená farba a zároveň výstražná ikona vás upozorní, že doména nie je zabezpečená službou DNSSEC.
V niektorých webových prehliadačoch môže existovať aj rozšírenie, ktoré umožní si podobnú informáciu pozrieť priamo cez prehliadač.
Kde ho môžem získať pre svoju doménu?
Štatistiky .sk domén s DNSSEC
Ako technicky funguje DNSSEC?
DNSSEC používa asymetrické šifrovanie – jeden kľúč pre zašifrovanie a druhý kľúč na dešifrovanie. Podobný princíp sa používa pri šifrovaní a elektronickom podpisovaní emailov (OpenPGP, S/MIME). Držiteľ domény, ktorá používa DNSSEC, vygeneruje dvojicu kľúčov – privátny a verejný kľúč (resp. mu ich zabezpečí jeho registrátor). Technické údaje o doméne sa následne elektronicky podpíšu privátnym kľúčom. Verejný kľúč, ktorý je uložený u nadriadenej autority jeho domény, sa potom používa na overenie pravosti technických údajov prostredníctvom overenia platnosti tohto podpisu v celej hierarchii nadradených podpisov až ku koreňovému.
Po spustení DNSSEC sa podpíšu technické dáta domény najvyššej úrovne .sk a verejný kľúč k tomuto podpisu bude správcom registra, t.j. SK-NICom, odovzdaný nadriadenej autorite – správcom celosvetových koreňových serverov DNS. Vytvára sa tak hierarchia, ktorá zabezpečí dôveryhodnosť údajov, pokiaľ nie je v žiadnom svojom bode porušená, t.j. chybná alebo nenastavená a teda všetky elektronické podpisy sú v poriadku.
Bezpečnostné úskalia systému DNS
Keď na začiatku 80-tych rokov vznikol systém DNS, nekládol sa mimoriadny dôraz na bezpečnostné mechanizmy tohto protokolu. Vtedajšie počítače boli neporovnateľne menej výkonné, asymetrická kryptografia (s použitím dvojice verejných a súkromných kľúčov) bola ešte len novým konceptom a celosvetová počítačová sieť bola oveľa menšia s menším počtom relatívne pripojených ľudí a inštitúcií, ktoré sa navzájom poznali. V ostatných 30-tich rokoch došlo k dramatickému rozšíreniu používania internetu a protokol DNS sa stal zraniteľným, čo si vyžiadalo vznik a použitie dodatočných bezpečnostných mechanizmov.
Existuje niekoľko hlavných bezpečnostných rizík DNS systému:
- Únos DNS (DNS hijacking): Počítač otvára webstránku používajúc IP adresu, ktorú mu na vyžiadanie zašle DNS server. V prípade DNS únosu útočník zmení DNS nastavenia na počítači tak, že kedykoľvek počítač zašle DNS dopyt, aby preložil IP adresu namiesto pravého DNS servera u poskytovateľa internetu a počítač sa tak spojí s falošným DNS serverom, ktorý kontroluje práve útočník. K takémuto útoku dochádza spravidla, keď je počítač infikovaný škodlivým kódom, napríklad trójskym koňom meniacim DNS. Škodlivý kód po infikovaní počítača zmení nastavenia DNS a nahradí adresu autentického DNS servera adresou škodlivého servera. Dôsledkom toho je, že zasiahnutý počítač nedostane pravú IP adresu požadovanej stránky, ale škodlivú IP adresu, smerujúcu na stránku útočníka a webový prehliadač tak zobrazí škodlivú webstránku.
- Otrávenie vyrovnávacej pamäte DNS (DNS Cache Poisoning): O „otrávení vyrovnávacej pamäte“ DNS (DNS cache) hovoríme vtedy, keď sú v nej namiesto autentického záznamu uložené škodlivé dáta. Keď napr. zadáme adresu „sk-nic.sk“ po prvý raz, náš počítač zašle DNS dopyt adekvátnemu DNS serveru a odpoveď si uloží do svojej tzv. vyrovnávacej pamäte DNS spolu s časovým údajom o tom, dokedy je tento záznam platný. Ak znova zadáme počas daného časového úseku „sk-nic.sk“, náš počítač sa už neopýta DNS servera, ale vyberie IP adresu z vyrovnávacej pamäte DNS. Pri otrávení vyrovnávacej pamäte využívajú DNS útočníci niektoré škodlivé triky, aby prinútili počítač uložiť si škodlivé podhodené DNS záznamy obsahujúce IP adresy škodlivých stránok, ktoré kontrolujú útočníci. Čo sa potom môže pri ich použití stať je zrejmé.
- Elektronická pošta: Keď sú e-mailové správy zasielané z jedného servera na druhý, poštové servery takisto zasielajú DNS dopyt, aby získali IP adresy poštových serverov relevantných pre e-mailové adresy príjemcov. Aj tu môžu útočníci uplatniť svoje škodlivé metódy na prinútenie poštových serverov k presmerovaniu všetkej alebo vybranej elektronickej pošty na servery útočníka, pričom útočníci môžu pochopiteľne následne prečítať všetky (citlivé) údaje obsiahnuté v e-maile.
Tento výpočet bezpečnostných rizík pritom nie je úplný, existujú aj ďalšie hrozby.
DNSSEC napomáha v ochrane pred týmito, ale aj inými formami útoku.